Topics on Top of CISO's Minds July 2024
This is an Executive Report of the Senior Security Leader cohort on July 17, 2024. This report captures the essence of the discussion, focusing on the major topics, challenges, and potential solutions discussed by the participants, who were supported by SME and LinkedIn Top Information Security Voice Petri Kuivala.
Fourteen senior security leaders participated actively in the conversation about the following topics:
1. How to best understand the value of Cyber Security
2. How to build a framework for setting priorities in an enterprise
a. What is the objective of such a large activity (Budget, resources, controls)
3. SEC Disclosure rules and materiality
4. What is the perfect structure for Board Reporting
5. Modernizing Security Awareness
Did you know?
The Value of Cyber Security
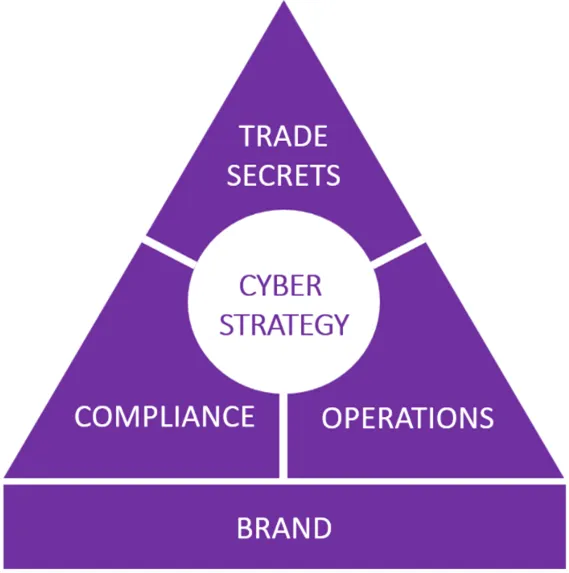
In the past, Petri summarized the value of cyber emerging through visual aspects with this diagram.
Leveraging Brand as a Sales Force Multiplier
It logically depends hugely on the company, how these areas break down, and how the value is created.
The Brand could be seen as a Force multiplier for Sales that creates trust and loyalty between the company and its customers. Depending on the industry the company is in, the value of such a multiplier changes dramatically.
Long ago, when the Nokia brand was the 5th recognized brand in the world, we made a calculation in the company to see how many single leakages of non-published phone models impacted sales.
We had Marketing, Sales, Legal, and the CEO in the task force (CEO as a reviewer), and we used the material when we built a case for the FBI. The result was 300M$ per leak, but we must also remember that it was the time when the company produced 25 phones/second for 24x7x365.
Petri Kuivala’s Recommendation
My guidance would be to have a deeper conversation about your brand value with your C-level and think in advance how Cyber & Information leakages could impact it.
Achieving Stability: Reducing Annual Downtime with Cyber and Operational Strategies
As said during the cohort with the NXP, calculating the Value of Downtime hours at a factory was easy.

I cannot disclose the NXP downtime numbers, but with Nokia, we reduced the Annual Downtime from 600h to 40h in a few years. This was not emerging from Cyber, but many Cyber activities contributed to the stability of the factories beyond just reducing the Cyber issues.
Protecting Future Competitiveness: Lessons on Innovation Safeguarding from CTO Insights and R&D Collaboration
I consider them “Delayed Operations,” i.e., if you lose your future competitiveness assets now, you will generate less revenue in a few years as someone else is “eating it” with your recipe that was supposed to be the next killer thing. My best “friend” here was the CTO. I learned much from him about the other mechanisms to protect innovation beyond Security and IPR.
If you do not have a real-life incident to motivate the investments, then deep discussions with the R&D folks to understand the business risks is worth of “thousand rabbits.” 😊
The Impact of Hard Compliance: How Regulatory Certification Secures Business Continuity and Market Access
It depends on whether it is “Soft Compliance” or “Hard Compliance”. With Hard Compliance, I mean regulation that can derail your participation in a business. For example, x% (quite large %) of the NXP product portfolio is sold to customers who would not buy it if the company did not have a certificate.
Discussions at the Roundtable: Effective Cyber Risk Governance
Wherever you have a risk committee where you can have direct conversations with the CFO, CLO, COO, and or their teams, make sure you are not the one who defines the Value of the Cyber alone. CISO can influence the conversation and pitch it up well, but at the end of the day the conversation around the “above triangle picture” should lead to a consensus where the business leaders guides CISO about the value, and where CISO is the SME for Cyber probabilities/weaknesses.
In larger companies the CRG implementations supports this dialogue pretty well, but implementing great CRG process is far from easy.
Strategic Investment and Resource Prioritization: Navigating CRG Process Challenges
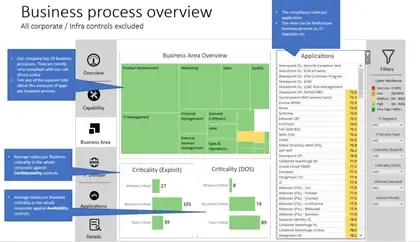
I used the CRG process to help with investment and resourcing priority setting, but I must admit running a reliable CRG process is more than hard. I can elaborate on it in a one-on-one call if you want to. Here is one of the best views of one company through CRG reporting.
As discussed in the call, it is recommended that we discuss this with players like AIG, Deloitte, PWC, etc. They have good approaches, but I must warn you: They are far from cheap.
As said in the call, investing 100k in a study with one of them can easily dramatically impact one's budget. Do not surprise your C-level with such a report, but bring them along early enough.
Effective Cybersecurity Reporting: Best Practices for Communicating Risks, Trends, and Successes to the Board
One of the participants had an excellent “recipe” for reporting:
1. Start with the “What’s in the news” segment.
a. What was the thing
b. How did it impact the victim company
c. Your risk level assessment, and
d. Action plan to reduce the risk even further.
2. Report the Security incident trend and logically disclose any Material or close-to-material cases to the BoD.
3. Report about your successes during the last period.
4. No so many KPIs, especially if they are not well linked to the business objectives.
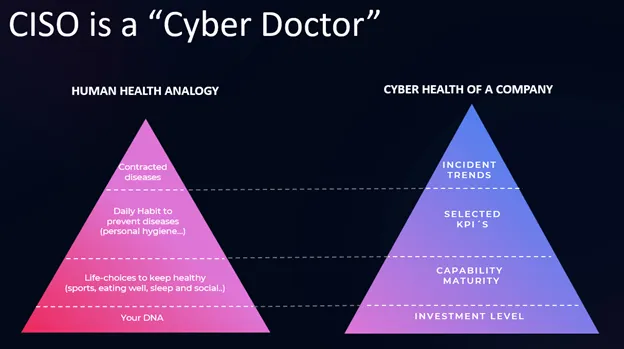
CISO as Cyber Doctor: Using Analogies and Frameworks to Educate the Board on Cybersecurity Health
I like to see CISO as a Cyber Doctor and use analogies when reporting some KPIs. This diagram reflects the overall framework that I have successfully used with many board members.
Mostly highlighting and educating the BoD members that “having a disease does not mean you are in bad condition”.
Beyond of this comment, I´m 100% aligned with the recipe disclosed above.
Modernizing Security Awareness Training
We did not have time to discuss this topic, but one participant asked it, and Petri has been advising one scale-up for a few years that has enabled the following companies to win CSO50 awards:
• 2023 – Qualcomm
• 2022 – AES
• 2021 – DocuSign
Cyberthreat Case Study Deep Dive
Access On-demandLearn as Petri Kuivala walks you through a real-life cyberattack case involving a nation state called Panda, which was related to a larger M&A case between two large companies. See the several-year hacking timeline and a high-level overview of how it happened and mistakes that could have been avoided.
Learn:
How to be prepared when the “s” hits the fan
How to be the successful CISO at the time of the storm
The most important things to do to prevent a cyberattack in the first place
Next Peer Roundtable Cohort - Tuesday, August 13, 2024 @ 1PM Eastern
Meet with Petri
Ask Petri Kuivala about any challenge you have. Petri works with boards, CISOs, vCISOs, global CISOs, VP Information Security, VP IT Security, Security Awareness Directors, Director of Security Awareness, Cyber Security Architect, Behavior and Culture, and Human Risk Managers, assisting them in discovering new thinking…. Click the button to access Petri's calendar.
Resources
Copyright © 2020- Peer Roundtables. All Rights Reserved

