Topics on Top of CISO's Minds April 2024
Peer Roundtable for Senior Security Leaders Executive Recap from 4/17/24
This is a summary of the Senior Security Leader cohort discussion during the Peer Roundtable on April 17, 2024. This executive summary captures the essence of the discussion, focusing on the major topics, challenges, and potential solutions discussed by the participants.
Did you know?
CYBERTHREAT CASE "STORY"
NEXT COHORT
SECURITY VALUATION PYRAMID
Flipbook View
Flipbook View
Key Discussion Points
Security Culture
- Most of the participants highlighted the power of positive enablement culture.
- We have talked for ages about moving from NO to KNOW-HOW; this movement is still in progress.
- Sharing the benefits and positive stories significantly impacts the user base and the management.
- At some point, we took the “safety team position at the end of the line.” Now, thanks to cyber's business importance and increasing positive approach, we are moving ahead.
- Using “Snowball Dogs” as scapegoats or other joint and relatable enemies has excellent power.
- The next step is to build systems that give positive feedback to users when they do the right thing. This would help them conditionalize good behavior.
- The next level would be to use AI to give immediate feedback if people report real attacks. That would have a huge motivation boost effect.
Artificial Intelligence
- Should it be used
- Using it for malicious purposes & defense purposes
- Biases it has
- How to handle sensitive information / PII
- It is used anyway, so how do we enable it?
- How can we better understand if vendors value providing AI instead of just labeling it? Here, the evidence-based conversation is beneficial.
Evidence-based Security
- How can we drive the Cyber Security implementation based on data instead of gut feeling?
- How to avoid liability/culpability (SolarWinds)
- How to integrate the Cyber Risk mgmt. With Enterprise Risk mgmt. And make it part of the normal ERM flow so the C-Level understands better.
Evidence-based Security
- We are still seen as a cost center in many organizations
- When establishing trust, having a positive enablement mindset and acknowledging what the C-level / their teams already are doing well will help.
- The standard view was to establish a good relationship with C-Level and discuss, e.g., around this framework:
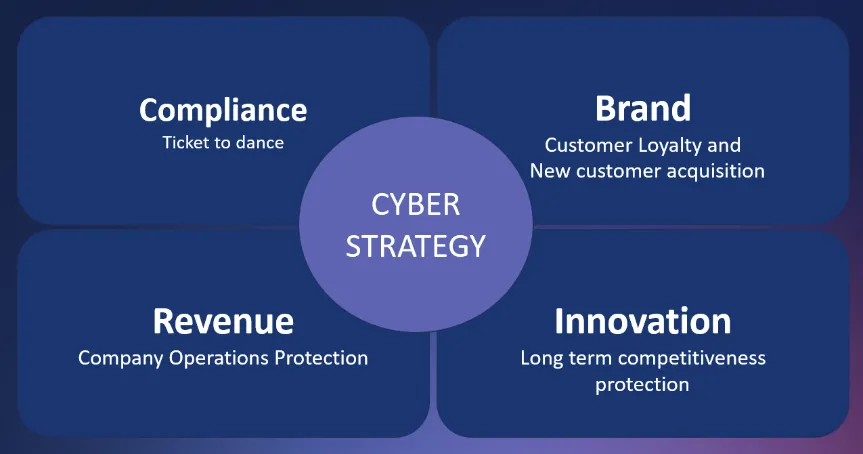
OT-Security
- We heard an extreme case of OT security, where the implementation times are very long and products are out of support when they are put into use.
- We agreed, though, that similar (not necessarily as extreme) cases exist in many other industries, such as Medical and Semiconductor.
Leveraging Outsights (what others know)
This peer roundtables was proven invaluable in fostering dialogue among senior security leaders, highlighting the importance of adaptability, collaboration, and strategic foresight in navigating the evolving cybersecurity landscape. You are encouraged to leverage the outsights gained in these discussions to enhance your insights into your organization's security posture and prepare for the challenges ahead.
Cyberthreat Case Study Deep Dive
Access on Demand
Learn as Petri Kuivala walks you through a real-life cyberattack case involving a nation state called Panda, which was related to a larger M&A case between two large companies. See the several-year hacking timeline and a high-level overview of how it happened and mistakes that could have been avoided.
Learn:
How to be prepared when the “s” hits the fan
How to be the successful CISO at the time of the storm
The most important things to do to prevent a cyberattack in the first place
Next Cohorts
Wednesday, May 15, 2024, at 1:00 PM Eastern
Tuesday, June 18, 2024, at 1:00 PM Eastern
Meet with Petri
Ask Petri Kuivala about the Cyberthreat Case Study or any of the resources available. He's also open to discuss your current challenges beyond what's provided. Click the button to go to Petri's calendar.
Resources
• Security Value Creation Pyramid: A framework for layering security initiatives in corporate settings, inspired by Maslow's hierarchy of needs. Provides a structured approach to prioritizing foundational safety measures and advanced value-creation strategies.
• Should CISO Report to CIO: What is essential regardless of the reporting structure.
• Enterprise Cybersecurity in Digital Business: by Ariel Evans: Guides CEOs, CISOs, and compliance managers on setting goals and addressing cybersecurity gaps within organizations.
• Evidence-Based Cybersecurity: by Pierre-Luc Pomerleau and David Maimon: Introduces an evidence-based approach to enhancing cybersecurity operations relevant for security professionals and policymakers.
Copyright © 2020- Peer Roundtables. All Rights Reserved
